For people in hurry get the code from Github.
In continuation of my earlier blog on spring-test-mvc junit testing Spring Security layer with InMemoryDaoImpl, in this blog I will be doing the following,
- Run a sample Jasig, deployed in tomcat instance
- Run a sample Spring security Calendar application with uses single signon to do authentication and authorization of the application
Setup of Central Authorization Service (CAS): Jasig
Central Authorization Service (CAS) is a Single Signon application used to authenticate and authorize an application for centralized user access control. Jasig is an opensource CAS application. In order for Jasig to work we need to enable SSL.
- As a first step, we will enable SSL for Tomcat 7, for that download and copy the certificates into <Tomcat home>/conf folder
<Connector SSLEnabled="true"
maxThreads="150"
port="8443"
protocol="HTTP/1.1"
scheme="https"
secure="true"
sslProtocol="TLS"
keystoreFile="${catalina.base}/conf/tomcat.keystore"
keystorePass="changeit"
truststoreFile="${catalina.base}/conf/tomcat.truststore"
trustStorePass="changeit"/>
- We need import p12 certificate in the browser for certificate handshake
- Build the code from cas-server-with-ldap project using maven command “mvn clean package” and deploy the war file in the target folder into <Tomcat home>/webapps folder
Run the Calendar application against CAS
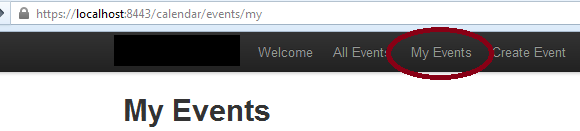
Build the code from spring-security-cas project using maven command “mvn clean package” and deploy the war file in the target folder into <Tomcat home>/webapps folder. Start the Tomcat instance. If you go to the calendar home page @ https://localhost:8443/calendar, you will see the webpage as below,
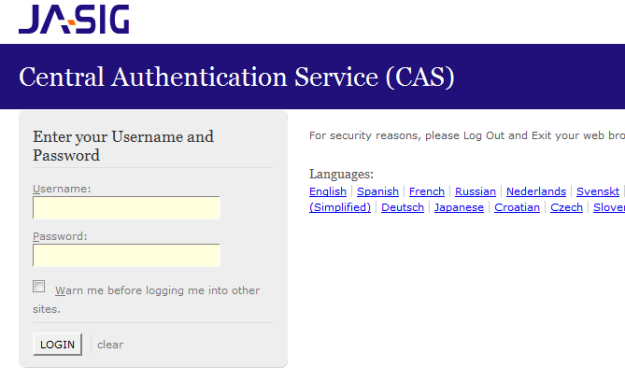
When you click on My Events we get the below Jasig page,
Enter login/password as user1@example.com/user1. You will get the access to your events.
When you log out, it will again redirect to Jasig logout page.
What is happening under the hood on Jasig side
Under the hood, Jasig CAS server is configured to work with inmemory LDAP as below,
<sec:ldap-server id="contextSource" ldif="classpath:ldif/calendar.ldif" root="dc=jbcpcalendar,dc=com" />
And mapping of LDAP attributes to CAS attributes happens in the below bean definition,
<!-- Bean that defines the attributes that a service may return. This example uses the Stub/Mock version. A real implementation may go against a database or LDAP server. The id should remain "attributeRepository" though. --> <bean id="attributeRepository"> <property name="contextSource" ref="contextSource"/> <property name="requireAllQueryAttributes" value="true"/> <property name="baseDN" value="ou=Users"/> <property name="queryAttributeMapping"> <map> <entry key="username" value="uid"/> </map> </property> <property name="resultAttributeMapping"> <map> <entry key="cn" value="FullName"/> <entry key="sn" value="LastName"/> <entry key="description" value="role"/> </map> </property> </bean>
Check the deployerConfigContext.xml under webapp/WEB-INF folder in the project for more details
What is happening under the hood on Calendar application
In the web.xml we need to include a SingleSignon listener as below,
<listener> <listener-class>org.jasig.cas.client.session.SingleSignOutHttpSessionListener</listener-class> </listener>
We need to define a casAuthProvider bean and include it in the authentication-manager in the security config as below,
<authentication-manager alias="authenticationManager"> <authentication-provider ref="casAuthProvider" /> </authentication-manager>
Refer src\main\webapp\WEB-INF\spring\security-cas.xml file for more details on casAuthProvider bean definition.
Maven dependency for Spring Security with CAS is as below,
<dependency> <groupId>org.springframework.security</groupId> <artifactId>spring-security-cas</artifactId> <version>3.1.0.RELEASE</version> <scope>compile</scope> </dependency>
I hope this blog helped you.
REFERENCE
Spring Security 3.1 by Robert Winch and Peter Mularien